Many banks and finance firms may not fully realise they could face substantial fines and penalties within a year if they do not significantly expand or adjust their testing capabilities.
In fact, the Digital Operational Resilience Act (DORA), which will come into force in January of 2025, will require the creation of new pressure tests and other critical testing infrastructure, a range of industry insiders have warned.
Banks, insurers and other financial services firms are therefore urged to urgently review and revamp their testing strategies as DORA is “not just a fire drill”, they said.
“Financial services firms and other entities that will must strengthen or build pressure test and implement the critical systems and protocols that will protect both operational and personal data from adverse manipulation, destruction or theft,” according to New York City-based Kris Lovejoy.
“If they don’t, they’ll be subject to sanctions and penalties, up to and including the C-suite and board of directors, in addition to operational and reputational damage,” she said.
Lovejoy is global security and resilience leader at information tech services multinational Kyndryl, the spin-off of IBM’s infrastructure services business in 2021 and a major developer of IT security testing solutions.

“The application of DORA safe protocols should not be considered as a fire drill.”
– Kris Lovejoy
DORA is among several recent and emerging regulations in the EU, created to enhance and standardise requirements for enterprise cyber resiliency.
The rules are specifically for financial entities operating across the EU 27 — including banks, insurance companies, credit agencies and more — and third-party service providers that serve them.
“Now regulatory compliance (and associated fines and legal fees) and cyber insurance repercussions will compound the effects of cybersecurity breaches,” Lovejoy explained.
DORA will come into force on January 17 of next year.
“Next January may seem like a distant target. But in the complex world of financial services information and communication technology (ICT), one year is hardly enough,” she told the HNS website.
“Firms must strengthen pressure test and implement critical systems and protocols. If they don’t, they’ll be subject to sanctions and penalties,” Lovejoy emphasised.
That sentiment is echoed by Fabio Colombo, head of Global Cybersecurity for financial services at Accenture.
Milan-based Colombo said in agreement that banks and other finance firms will need to update and change their testing capabilities, operating procedures and risk if they wish to be fully compliant with the EU’s new DORA framework.
DORA will also require operational reviews, system evaluations, more training and frequent audits, he added.

“DORA outlines the need for banks to fortify their digital defences.”
– Fabio Colombo
Colombo’s observations are not new. QA Financial stated in 2022 in a report that operational preparedness efforts needed to be stepped up in order to ensure that all participants in the financial system have the necessary safeguards in place ahead of DORA.
In conjunction with Accourt Payment Specialists and Reed Smith, Expleo and QA Financial gauged the prevailing sentiments of 39 traditional and challenger banks, asset managers, insurers, payment firms and other Fintechs in the UK and EU.
Steven Rackham, currently the chief technology officer for Financial Services at NetApp, based in London, also said financial services firms should start preparing harder for a major shift in the way they approach IT security and QA testing.
In fact, implementing DORA will be such a huge challenge for many financial services players that many banks and other finance firms may underestimate as it may require an overhaul of their current culture, he said.
“Preparing for any change in regulation is hard enough, but with the European Banking Authority yet to publish the final technical specification or a list of critical IT providers, businesses are effectively still in the dark in terms of the detail,” noted Rackham, who is also a financial services council member at industry group TechUK said that
Devil is in the detail
Last month, the European Commission has formally adopted a number of stipulations related to DORA.
The EU’s executive body issued a whole set of secondary legislation in February that set out detailed, technical rules specifying some of the key provisions of DORA.
Firstly, it has now been confirmed that DORA will introduce an ‘oversight framework’, which did not exist under pre-existing outsourcing regulations.
ICT third-party service providers that are designated as ‘critical’ will be made subject to regulatory scrutiny, largely overseen by the European Supervisory Authorities (the ESA), which are the European Securities and Markets Authority (ESMA), European Banking Authority (EBA) and European Insurance and Occupational Pensions Authority (EIOPA).
This approach allows the ESA to investigate and inspect providers in relation to IT security, risk management and governance issues.

“DORA will require going against conventional wisdom.”
– Steven Rackham
The framework also gives ESA the power to make recommendations and issue fines of up to 1% of the ICT third-party provider’s annual worldwide turnover.
Moreover, the EC also detailed the criteria “for the designation of ICT third-party service providers as critical for financial entities.”
In other words, it set out what ‘critical ICT providers’ are. In addition, the EU body also introduced a vast and fairly complex structure for oversight fees.
“DORA will require financial entities to report any major ICT incidents to their corresponding competent authorities via specific reporting templates in specifically prescribed timelines,” Lovejoy explained.
“Any reports must also include all the necessary details for the receiving competent authority to then ascertain the level of ICT incident and any possible cross cross-border impact posed,” she stated.
What does DORA cover?
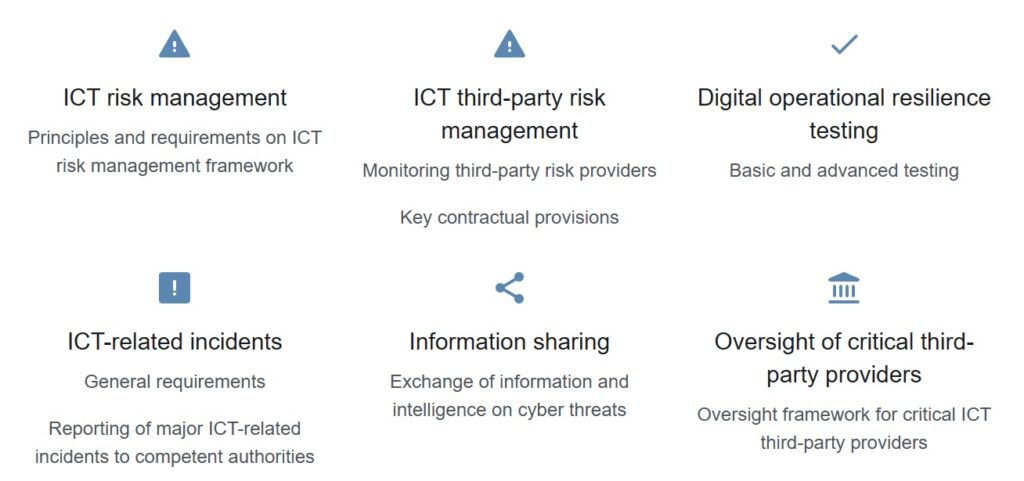
‘Critical’
To determine whether an ICT third-party service provider is ‘critical’ for banks, insurance firms and other financial entities, the ESAs will use sub-criteria in a two-step approach assessment.
Firstly, the ESAs will take into account important ICT services and the diversity and number of financial institutions that use those services.
This is primarily done to “filter the population of ICT third-party service providers and identify the most critical ICT third-party service providers.”
After this ‘first selection’ of ICT third-party service providers, a further in-depth analysis will be carried out that focuses on a range of sub-criteria.
So far, the EC has not set out these standards but has hinted that, in some cases, it will be left to individual member states to fill these gaps.
This prompted Colombo to say that banks and other financial services firm should not underestimate the changes that are needed ahead of DORA.
He pointed out that DORA’s first pillar, ICT risk management, “outlines the need for financial institutions to fortify their digital defences.”
Colombo stressed the new regulation emphasises not merely new standard cybersecurity measures, but also robust administrative procedures, internal controls, and risk assessments.
“In simpler terms, it’s about ensuring the digital infrastructure is solid, secure, and resilient against potential threats,” Colombo stated.
Regular testing
For banks, insurers and finance firms, regular testing of ICT systems to evaluate strengths and identify vulnerabilities “will now become of paramount importance, as results and subsequent plans to address any areas of concern will need to be shared with the relevant competent authorities,” Lovejoy said.
She stressed that, under DORA, financial entities will also be required to undertake annual basic testing, such as vulnerability assessments and scenario-based testing, whilst those considered to have a critical role in the financial system and their ICT providers will also need to undergo additional threat-led penetration testing every three years.
“Financial entities will be required to undertake annual basic testing, such as vulnerability assessments and scenario-based testing.”
– Kris Lovejoy
Finally, Lovejoy pointed out that DORA will require internal audit functions to review and potentially augment all their current plans and programs, as these will now need to pinpoint potential risks to financial entities via third-party ICT providers.
“This means that internal audit functions should be challenging their established risk-identifying process regularly, maintain a register of information related to all contractual agreements, and report to regulators annually,” she noted.
Lovejoy stressed that firms may opt to outsource their reporting obligations to a third-party, but “ultimately remain responsible for compliance with obligations under DORA.”
“The application of DORA safe protocols should not be considered as a fire drill, as proper planning for critical cyber activity requires considerable and regular training, senior management support and properly prepared security operations teams to be most effective,” she warned.
In summary, the new framework means a major change from the current regulatory approach.
Prior to DORA, the EU operational resilience and cybersecurity risk management governance model for financial firms was based on a disparate collection of national rules, guidelines, and practices that did not empower EU financial supervisors to impose uniform requirements on FEs nor to assess the risks arising from their dependence on TSPs.
“DORA tackles these disparities and uneven national regulatory or supervisory approaches,” Lovejoy said.
Rackham could not agree more.
“Gambling by taking a ‘wait and see’ approach is unlikely to impress the regulator,” he stressed.
“If being fully compliant by 17th January 2025 is unrealistic, demonstrable progress and having a clear plan to meet all requirements within a reasonable timeframe should mean escaping the harshest punishments,” Rackham concluded.
Stay up to date and receive our news, features and interviews for free
Our e-newsletter lands in your inbox every Friday. Sign up HERE in one simple step.
ALSO READ




